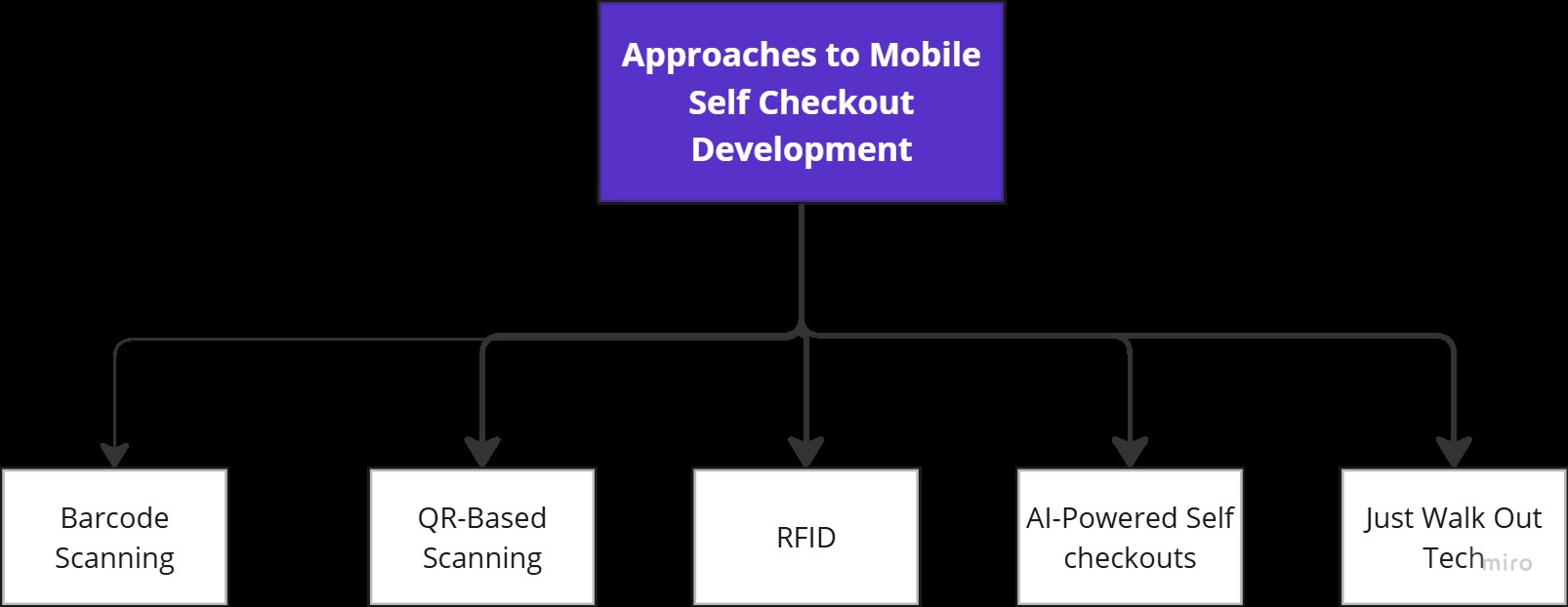
How AI and Deep Learning Models Power Object Detection
Modern object detection relies heavily on deep learning models that train on vast datasets to recognize patterns and features in visual data.
Two prominent architectures in this field are YOLO (You Only Look Once) and Faster R-CNN (Region-based Convolutional Neural Networks).
- YOLO: Known for its speed, YOLO processes images in a single pass, making it ideal for real-time applications like autonomous driving or live surveillance. It divides the image into a grid and predicts bounding boxes and class probabilities for each grid cell.
- Faster R-CNN: This model prioritizes accuracy over speed.
It uses a two-step process:
- First, it identifies regions of interest (ROIs) that may contain objects
- Then, it classifies and refines the bounding boxes for those regions.
Both of these models leverage convolutional neural networks (CNNs) to extract features from images, and so, detect objects with high precision.
Key Components of AI-Powered Object Detection
Three critical components make AI-powered object detection effective:
Image Recognition
The ability to classify objects within an image is foundational. Advanced algorithms can distinguish between thousands of object categories, from everyday items to specialized industrial equipment.
Real-Time Processing
Many applications, such as autonomous vehicles or security systems, require immediate analysis. Real-time processing ensures that object detection systems can deliver instant results without significant delays.
Accuracy
High accuracy is essential, especially in critical fields like healthcare or manufacturing. Deep learning models continuously improve their accuracy through training on larger and more diverse datasets, reducing errors like false positives or missed detections.
Use Cases of AI-Powered Object Detection
Waste Management
Automated Waste Sorting and Recycling
Traditional recycling facilities rely on manual labor or basic mechanical systems to separate materials like plastic, glass, and metal. AI-powered object detection is transforming waste management by automating the sorting of recyclable materials.
AI systems equipped with cameras and deep learning models can identify and categorize waste with remarkable precision.

Corporates in the waste management and recycling space, use AI-powered robots to sort recyclables at high speeds, significantly improving efficiency and reducing contamination in recycling streams.
Drone-Based Monitoring for Illegal Dumping
Illegal dumping of waste is a persistent problem in many regions. Drones equipped with AI-powered object detection can monitor large areas and identify illegal waste sites.
These systems can detect and report unauthorized dumping activities in real-time so authorities can take swift action. A real-world example is the use of drones by the UK Environment Agency. The agency has deployed AI-powered drones to monitor and combat illegal waste disposal in remote areas.
Manufacturing
Quality Control and Defect Detection
Product quality is one of the strongest success metrics in manufacturing businesses. And object detection systems really help maintain this quality and detect defects. These models inspect products on assembly lines to identify defects such as cracks, scratches, or misalignments.
Book a call
Such systems work faster and more accurately than human inspectors – which means consistent quality at speed and scale. Siemens uses AI-based visual inspection systems to detect defects in industrial components; this reduces manufacturing waste and improves their production efficiency.
Equipment Monitoring and Safety Compliance
Safety conditions and equipment functionality are an important aspect of workplaces in manufacturing facilities. Object detection can dramatically improve workplace safety by monitoring equipment and worker behavior.

We have AI systems that now detect unsafe conditions, such as machinery operating without safety guards or workers not wearing protective gear.
A notable example is NVIDIA’s Metropolis platform, is a framework that uses AI-powered object detection to monitor industrial environments and compliance with safety protocols.
Retail
Automated Checkout Systems
Retailers are increasingly adopting AI-powered object detection to streamline the checkout process. Automated systems can identify items in a shopping cart and generate a bill without the need for barcode scanning.
Amazon Go stores are a prime example of this technology in action. Their “Just Walk Out” system uses cameras and AI to detect items customers pick up. Once done with shopping, they can leave the store without waiting in the line for checkout.
Shelf Monitoring and Inventory Management
In the retail sector, object detection helps businesses, warehouse managers and inventory department executives overcome the challenges of shelf stocking and organization.
When used in connection to warehouse management systems, these object detection models monitor shelves in real-time, identify out-of-stock items and send alerts for misplaced products. This data helps retailers optimize inventory management and improve customer satisfaction.
Trax, a leading retail technology company, uses AI-powered cameras to track shelf conditions and provide actionable insights to their store managers.
Healthcare
Medical Imaging and Diagnostics
AI-powered object detection plays a crucial role in medical imaging by helping healthcare professionals identify abnormalities in X-rays, MRIs, and CT scans.
These systems can detect conditions such as tumors, fractures, or infections with high accuracy. Doctors can then utilize early diagnosis, prioritize urgent cases and provide treatment accordingly.
Patient Monitoring and Safety
In hospitals, AI-powered object detection improves patient safety by monitoring movements and detecting emergencies. For instance, systems can identify if a patient has fallen or is in distress and alerts staff immediately. Cameras equipped with AI facilitate compliance with hygiene protocols, such as handwashing, to prevent infections.
A real-life example is the use of AI-powered monitoring systems by companies like Care.ai, which provide real-time insights into patient activity and safety in healthcare facilities.
Agriculture
Crop Monitoring and Pest Detection
Farmers are leveraging AI-powered object detection to monitor crop health and detect pests or diseases early. Drones equipped with cameras and AI algorithms can scan fields, identify problem areas, and provide actionable insights.
This helps farmers take targeted actions, such as applying pesticides only where needed, reducing costs and environmental impact.
Automated Harvesting Systems
AI-powered object detection is also revolutionizing harvesting by enabling machines to identify and pick ripe fruits or vegetables. These systems use cameras and sensors to detect the size, color, and ripeness of produce, ensure efficient and damage-free harvesting.
Agriculture corporates are now using AI-powered robotic harvesters that can pick strawberries with precision, address labor shortages and increase productivity.
Transportation and Logistics
Warehouse Automation and Package Sorting
In logistics, AI-powered object detection is optimizing warehouse operations by automating package sorting and tracking. Cameras and AI systems together can identify, categorize, and route packages to their correct destinations, reduce errors and speed up delivery times.
A notable example is Amazon’s fulfillment centers, where AI-powered robots and cameras work together to manage millions of packages daily with remarkable efficiency.
Autonomous Vehicle Navigation
Autonomous vehicles rely heavily on AI-powered object detection to navigate safely. These systems detect and classify objects such as pedestrians, vehicles, traffic signs, and obstacles in real-time. This helps selfdriving cars to make informed decisions.
Automobile giants like Tesla and Waymo use advanced object detection models to power their autonomous driving systems and bring us closer to a future of fully self-driving vehicles.
Security and Surveillance
Intruder Detection and Crowd Monitoring
AI-powered object detection enhances security by identifying intruders or unauthorized individuals in restricted areas. Surveillance systems equipped with AI can analyze video feeds in real-time, detect suspicious behavior and trigger alerts.
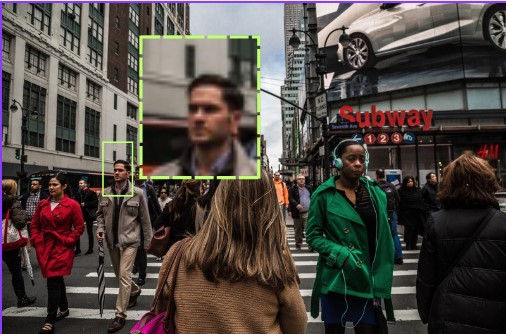
Additionally, these systems are used for crowd monitoring in public spaces, most importantly to secure and maintain the safety during large events. We now have cameras that work on the blend of IoT and object detection to detect intruders and monitor crowd density, prevent incidents and maintain order.
Anomaly Detection in Public Spaces
Beyond intruder detection, AI-powered systems can identify unusual activities or objects in public spaces, such as unattended bags or aggressive behavior. These systems analyze patterns and flag anomalies, enabling quick responses from security personnel.
Municipal organizations in cities like New York use cameras powered by object detection that help law enforcement detect and respond to potential threats in real-time.
Construction
Safety Compliance Monitoring
Construction sites are inherently risky environments, and AI-powered object detection improves their safety by monitoring compliance with safety protocols.
For instance, cameras with AI can detect if workers are not wearing helmets, safety harnesses, or other protective gear. They can also identify unsafe conditions, such as unguarded machinery or hazardous zones. Companies like Smartvid.io use AI to analyze construction site footage and ensure adherence to safety standards, reduce accidents and improve workplace safety.
Resource and Equipment Tracking
AI-powered object detection tracks the location and usage of tools, machinery, and materials, optimize resource allocation and reduce losses.
Benefits of AI-Powered Object Detection
AI-powered object detection offers transformative benefits across industries, enable businesses to:
- operate more efficiently
- save costs
- enhance safety
- make faster and better decisions
Below, we explore these benefits with concrete examples and data to illustrate their impact.
Accuracy and Efficiency
AI-powered object detection significantly improves operational efficiency and accuracy by automating tasks that were previously manual or error-prone.
Let’s take the example of manufacturing. AI systems inspect thousands of units per hour with near-perfect accuracy.
Several electronics manufacturers use AI-powered visual inspection systems to detect defects in smartphone components. These systems can inspect over 10,000 units per hour with an accuracy rate of 99.9%, far surpassing human capabilities. This level of precision reduces rework, minimizes waste, and dramatically improves product quality.
Cost Savings through Automation
Automation powered by AI-driven object detection reduces labor costs and operational expenses. For instance, in retail, automated checkout systems like those used in Amazon Go stores eliminate the need for cashiers.
Let’s break down the cost savings:
- A typical retail store employs 10-15 cashiers, each earning an average of $15 per hour.
- Over a year, this amounts to 600,000−900,000in labor costs.
- By implementing AI-powered checkout systems, stores can save up to 80% of these costs and reinvest the savings into other areas of the business.
Similarly, in agriculture, AI-powered systems like weed detection robots reduce herbicide usage by 90%. Farmers save thousands of dollars annually.
Enhanced Safety and Compliance
AI-powered object detection enhances workplace safety by monitoring environments and ensuring compliance with safety protocols.
For example, in construction, AI systems can detect if workers are not wearing helmets or safety harnesses, and reduce the risk of accidents.
We’ll give you example from a product we developed earlier in 2024, an IoT-enabled and AI-powered video application which uses advanced artificial intelligence models to analyze construction site footage and flag safety violations. Here are findings from their case studies.
In one case, a construction company reported a 30% reduction in safety incidents after implementing AI-powered monitoring. While they maintain safety and protection for workers, they also reduced costs associated with workplace injuries, which can average $40,000 per incident in medical and legal expenses.
In healthcare, AI-powered monitoring systems ensure compliance with hygiene protocols, such as handwashing, and reduce the risk of hospital-acquired infections. Hospitals using these systems have reported a 20-25% improvement in compliance rates.
Real-Time Decision-Making Capabilities
AI-powered object detection enables real-time decision-making, empowers employees and stakeholders to act quickly and effectively. For example, in transportation, autonomous vehicles use object detection to navigate roads, detect obstacles, and make split-second decisions to avoid accidents. Tesla’s Autopilot system processes data from cameras and sensors in real-time, making decisions within milliseconds to prevent collisions.
In retail, AI-powered shelf monitoring systems provide real-time data to store managers, enables them to restock items before they run out.
Challenges and Limitations in AI-Powered Object Detection System
While AI-powered object detection offers immense potential, it also faces several challenges and limitations that businesses have to overcome before they can fully adopt and implement such systems. Here are key issues our clients have reported during their discovery sessions.
High Computational Requirements
AI-powered object detection models, especially deep learning-based ones, require significant computational power. For example, training a YOLO (You Only Look Once) model on a large dataset can take days or weeks, even on high-end GPUs. That’s why it’s a resource-intensive investment for smaller organizations.
Need for Large, Labeled Datasets
Training accurate object detection models requires vast amounts of labeled data. For instance, creating a dataset for medical imaging might involve annotating thousands of X-rays, which is time-consuming and expensive, and often requires expert input.
Privacy and Ethical Concerns in Surveillance
The use of AI-powered surveillance raises privacy issues, as seen in cities like London, where facial recognition systems have sparked debates over mass surveillance and individual rights.
Balancing security and privacy remains a challenge with using artificial intelligence in public-facing systems – but development, implementation and compliance to AI governance frameworks have helped.
Integration with Existing Systems
Many niche industries, as well as businesses operating within, rely on legacy systems that are not compatible with modern AI solutions.
For example, integrating AI-powered object detection into older manufacturing equipment often requires costly upgrades or replacements.
Bias in AI Models
AI models can inherit biases from training data, leading to inaccurate or unfair outcomes.
For instance, object detection systems used in law enforcement have been criticized for misidentifying individuals from certain demographic groups, which largely raises concerns about fairness.
Environmental Impact
Training and running AI models consume significant energy and contribute to carbon emissions.
For example, training a single large AI model can emit as much CO2 as five cars over their lifetimes, which means with more AI solutions, we need better practices for sustainability, green technology frameworks and large-scale adoption of sustainable tech practices.
Future Trends and Opportunities in Adopting Object Detection System
With several emerging trends and opportunities poised to reshape industries, the future of AI-powered object detection is bright. Here are seven key trends that are redirecting how AI will pose a major transformative impact on the tech and global industries.
Advancements in Edge Computing for Real-Time Processing
Edge computing allows AI models to process data locally on devices, which reduces latency and facilitates real-time decision-making.
The quickest adoption example here is from Dubai’s Smart City initiatives. The framework encourages edge-based AI systems for real-time traffic monitoring and management and no wonder the emirate has dramatically improved urban mobility.
Integration with IoT and 5G for Smarter Systems
Combining AI-powered object detection with IoT devices and 5G networks makes smarter, interconnected systems.
In the US, companies like Verizon are deploying 5G-enabled AI solutions in manufacturing to monitor equipment and optimize production lines in real-time.
Expansion into New Industries and Applications
AI-powered object detection is expanding into niche industries like aquaculture and mining. In Norway, AI systems are being used to monitor fish health in aquaculture farms, while in Australia, mining companies use AI to detect equipment failures and improve safety.
Role of Generative AI in Improving Object Detection Models
Generative AI, such as Generative Adversarial Networks (GANs), create synthetic training data, improve the accuracy of object detection models.
For instance, NVIDIA’s synthetic data generation tools are helping autonomous vehicle developers train models in diverse virtual environments.
Adoption of Explainable AI (XAI)
Explainable AI is gaining traction as industries demand transparency in AI decision-making. In the EU, regulations like the AI Act are pushing companies to adopt XAI techniques, which further facilitate object detection systems to provide clear and interpretable results.
Focus on Sustainability and Green AI
Researchers and companies are developing energy-efficient AI models to reduce environmental impact. Google’s TensorFlow Lite helps deploy lightweight object detection models on low-power devices which is ultimately making AI more sustainable for everyone.
Collaboration Between Governments and Private Sector
Public-private partnerships are driving innovation in AI-powered object detection. In Singapore, the government is collaborating with tech companies to deploy AI-powered surveillance systems for urban planning and disaster management.
Leverage Object Detection Technology to Revolutionize Your Business
The potential of object detection goes beyond the industrial ad business applications you have come across in this article. The applications, and their impacts are vast and the journey has just started here. For businesses like yours that’s always planning to take the lead, the next step is clear: adopt and integrate AI-powered solutions, like object detection, to plan your next digital transformation campaign.
At Techlancers, we specialize in developing cutting-edge tech products. We go beyond mobile apps and custom – we empower B2C and B2B clients to plan their next business leap with innovation. With strong expertise in AI and machine learning, we create advanced solutions that are both: sustainable and scalable – a dynamic duo that makes our clients’ businesses monetization-ready.
Ready to develop the next game-changing AI solution?
Discuss your epic idea with us and we’ll take it from there with a strong research-rich proposal, monetization strategy and project plan.
Book a call




 Consulting
Consulting Development
Development Growth
Growth